1. Risk Assessment:
We will calculate the quantitative or qualitative value of risk related to your potential IT information security issues. This can be especially useful when applied to new projects, such as assessing the risk of adding functionality to an intranet or adding servers with sensitive information to a network. As computing resources move off-premise, we can analyze this impact on the overall security as well.

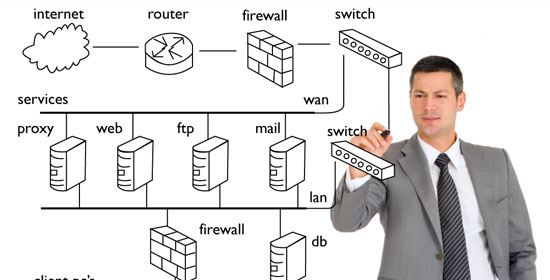
2. Security Architecture Review/Creation:
We provide a gap analysis of your existing security architecture. We are experts in building and implementing architectures that improve security and accommodate change to ensure your data is segmented, protected, and remains safe.
3. PCI-DSS Preparation and Remediation:
For organizations that deal with payment cards and cardholder data, we provide expert guidance with the Payment Card Industry Data Security Standard. Whether it involves preparing your organization to accept credit cards or remediation following a PCI audit, we have the capability to address any PCI related need.


4. Mobile Security:
With the rise of BYOD, the number of devices that touch a network is increasing rapidly. With Cal Net’s solutions, every device that is allowed to touch the corporate network can have policies enforced and may be managed for optimal IT information security and tracking.
5. Disaster Recovery/Business Continuity Planning:
When disaster strikes, it’s vital to have a plan in place so your downtime is as brief as possible and so that the amount of loss you suffer is as limited as possible. We provide the best data recovery Los Angeles has to offer. As a leader in disaster recovery solutions, we will craft a disaster recovery and business continuity plan tailored to your recovery time and recovery point objectives, within a budget that is right for you.


6. Data Classification:
We provide a comprehensive solution to find, classify, and protect vital data. We help ensure your information is protected from loss or theft, as well as ensure compliance with privacy laws or other compliance requirements governing your business. We are experts in HIPAA compliance, Sarbanes Oxley, and PCI, and we ensure your organization implements best-in-class processes and procedures, adhering to all regulatory requirements.
7. Incident Response:
When your business suffers an incident such as a virus or data leak, we provide a prompt and expert response, including a forensic analysis of what went wrong (and how to prevent it from happening again).


8. Security Awareness & Education: Security starts
with you.
We know how to talk about IT information security so every employee understands his or her part. We can educate your team about specific policies and procedures, as well as communicate best practices that maintain ongoing information security and risk management in Los Angeles.
9. Security Control Implementation:
The best way to address a breach is to stop it before it occurs. We analyze your security needs and recommend safeguards appropriate to your business and data. We then implement the appropriate security devices, including data loss prevention software, intrusion prevention and detection systems, application whitelisting, web application firewalls, and endpoint secure data protection.


10. Log Setup and Analysis:
A tool is only as good as the craftsman who uses it. We proactively monitor your environment to keep your environment safe. We set up security logs and analyze them on affected devices to determine if there are anomalies or exploitation attempts.
NETWORK SECURITY TO ENSURE PROPER DATA PROTECTION, ENCRYPTION AND LIMIT DATA THEFT
Network Operations
Network defense, perimeter protection, monitoring, policy development and implementation, and intrusion detection
Security Engineering
Policy development and implementation, mitigation support, and design of security layout and architecture
Certification and Accreditation
NIST and DoD policy and security best practices
guidance, DIACAP, eMASS and
MCCAST experience
Anti-Phishing
Phishing testing, education, training, forensic analysis, threat detection, and implementationof countermeasures
Cyber Threat Intelligence
Analyze threats, correlate analytical findings to ascertain attributable information regarding cyber groups and monitor indications and
warnings
Vulnerability Assessment
Security Test and Evaluation, Independent Verification and Validation, Risk Analysis, Manual test case development, and Automated tool development
Penetration Testing
External and internal scans, perimeter assessment, application testing, network enumeration, threat analysis and reporting
Forensics and Malware
Computer Forensics, mobile Forensics, network forensics, intrusion investigations, incident response, reverse engineering, and malware analysis
IA Support and Sustainment
IAVA Management, POA&M maintenance, annual security reviews, FISMA compliance, and incident response

